Introduction
Welcome back to our “Networking for Hackers” series! Today, we’re exploring Part 5, where we’ll solve the mysteries of TCP/UDP handshakes, Ports, and Protocols. These are like the secret codes that computers use to chat with each other online.
So, let’s jump right in and uncover the inner workings of internet communication!
TCP
TCP, short for Transmission Control Protocol, is a key part of how computers communicate over the internet. It’s like a reliable system that ensures messages sent between computers get to where they’re supposed to go without getting jumbled up or lost along the way. 📬 Imagine it as a well-organized postal service for digital data, making sure everything arrives safely and in order. 🌐
TCP 3-Way Handshake
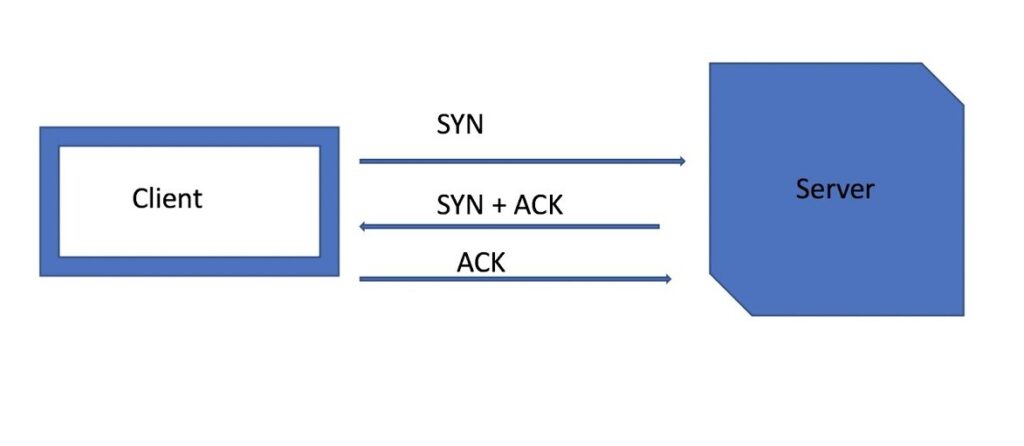
The TCP three-way handshake is like a discussion between two computers before they start sending data to each other. Here’s how it works:
- SYN (Synchronize): The first computer (let’s call it Computer A) sends a message to the second computer (Computer B) saying, “Hey, I want to talk to you!” This message includes a special code called a SYN (synchronize) flag.
- SYN-ACK (Synchronize-Acknowledge): Computer B receives the message from Computer A and responds with its own message. It says, “Sure, I’m here! Let’s chat.” This message contains both a SYN flag to synchronize and an ACK (acknowledge) flag to acknowledge the message from Computer A.
- ACK (Acknowledge): Finally, Computer A gets the message from Computer B and responds with an acknowledgment. It says, “Great, I got your message! Now we’re ready to talk.” This completes the handshake, and both computers can start sending data back and forth with confidence that they’re connected and ready to communicate.
So, in simple terms, the TCP three-way handshake is like a introduction between computers before they start swapping data, ensuring that both sides are ready and willing to communicate.
User Datagram Protocol (UDP)
UDP, or User Datagram Protocol, is a communication protocol that is a part of the TCP/IP protocol suite used in computer networks. Unlike TCP, UDP is connectionless, which means it does not establish a direct connection before sending data. Instead, UDP just sends data packets without verifying whether they arrive at the destination or in the correct order. This makes UDP faster than TCP, but also less reliable, as there is no error-checking or retransmission of lost packets. UDP is usually used for time-sensitive applications such as streaming media, online gaming, and VoIP (Voice over Internet Protocol).
What is Port?
A port is like a door or entrance on a computer or network device that allows communication between different applications or services. It’s a numbered endpoint that helps direct incoming and outgoing data to the right place, kind of like a street address for internet traffic.
The total number of ports that exist is 65,536. These ports are divided into different ranges, including well-known ports, registered ports, and dynamic or private ports.
Well-known ports: 0 – 1023
Registered ports: 1024 – 49151
Dynamic ports: 49152 – 65535
Most Common Ports
As a penetration tester or ethical hacker you should be familiar with the common ports and protocols used by services.
| Port Number | Service | Transport Protocol |
|---|---|---|
| 20 | FTP Data Transfer | TCP |
| 21 | FTP Control | TCP |
| 22 | SSH | TCP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 53 | DNS | TCP/UDP |
| 67 | DHCP Server | UDP |
| 68 | DHCP Client | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 119 | NNTP | TCP |
| 123 | NTP | UDP |
| 143 | IMAP | TCP |
| 161 | SNMP | UDP |
| 443 | HTTPS | TCP |
| 465 | SMTPS | TCP |
| 514 | Syslog | UDP |
| 587 | SMTP Submission | TCP |
| 993 | IMAPS | TCP |
| 995 | POP3S | TCP |
This table lists some common port numbers along with the corresponding services and transport protocols they use.
- When a service has a specific port open, it’s considered to be actively “listening” for connections on that port.
- Once a connection is established by a service, the port enters a state known as “established.”
Conclusion
As we wrap up our series, remember the essential computer networking topics covered here, crucial for hackers and penetration testers. While this is the final part, there’s more to explore if you’re eager to learn. Understanding these concepts deeply enhances your ability to exploit network systems.
Stay tuned for our upcoming List Of Practical Hacking Series. Keep exploring and hacking!
Subscribe to Our FREE Daily Newsletter For Future Series Updates!!
New here? Read “Networking For Hacker’s | Part-1” & Follow Us on Instagram, LinkedIn, Facebook



